As per SDK we are making the JWT call from https -
makeAPICall(’/oAuth/token/jwtgrant’, args, optCb);
I could see httponly in request headers but ‘Secure’ flag is not enabled. I think this flag should set it in the server. Can you please help on this issue?
As per below image we expect secure flag enabled.
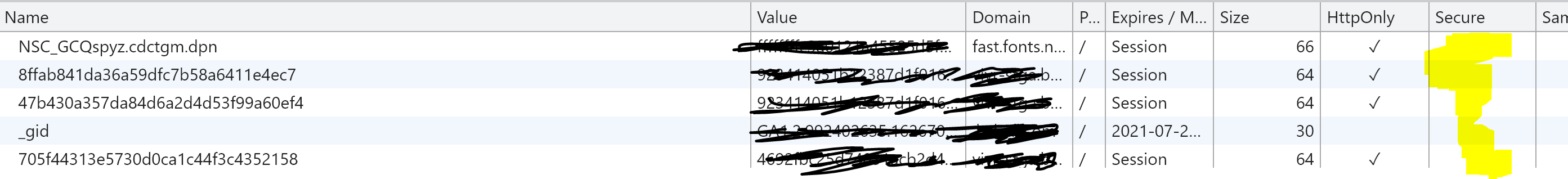
@senthilkumar.muruges
I am not sure I understand your question well. In general the jwt generation service is owned by user or customer. Jwtgrant is a more service which authenticates the user against the app configured on the bot.
If you are using an on premise set up you will need to check with your local administrator to ensure https is used. If you are using our SaaS are you taking about the jwt token generation sts service or jwtgrant?
Please describe the issue in more details.
Thanks for your Response Swagata.
yes we are on https only. I am talking about jwtgrant. Cookies are generated in that call with ‘httponly’ flag but missing ‘secure’ attribute. We want to include that as well.
making the request to botkit => /bot/jwt/get for the token
this response is like -> httponly not included the secure flag.
Yes We are using it in https.
i could see ‘Httponly’ is enabled but unable to add the secure flag.
@senthilkumar.muruges
Thanks for the responses. Is the business need to store the jwt token itself as cookie? Jwtgrant just authenticates the jwt token.
@senthilkumar.muruges
in the meantime, while you state the business use case, here are some more inputs.
Secured cookies cannot be read by JavaScript. Users typically face this issue for bots hosted within portals like service-now, etc. There, the user login tokens are stored in the secured cookie, which cannot be sent across to the bot - neither as custom data nor as part of jwt payload. As such users will be prompted to log-in again in the bot through api call authorization.
You can refer to Restrict access to cookie section here https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
We are not trying to read. After the jwtgrant from https we could see the cookies as httponly in browser but missing secure attribute. we just want to secure flag enabled in the applicate cookie.
from the server response i could see this one. ‘secure’ attribute needs to be there as per security standard.
‘set-cookie’: [ ‘XXXXXXXXXXXXXXXXXX=xxxxxxxxxxxxxxx; path=/; HttpOnly’ ]
@senthilkumar.muruges
Are you taking about the start call cookie? for jwtgrant I don’t see anything when we use our web-sdk.
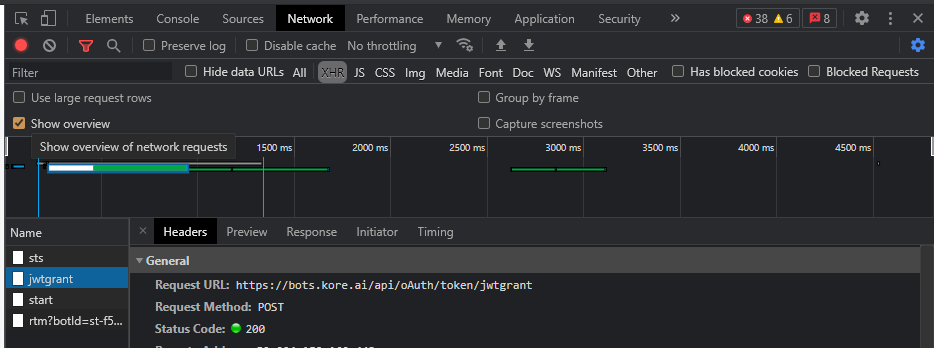
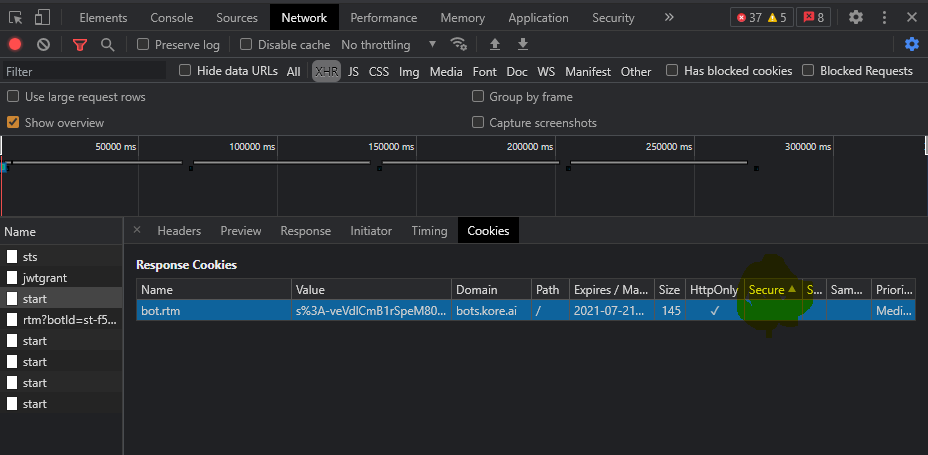
Also are you using/refering to our websdk or you are using bots.kore.ai bot builder?
yes, i think during the start call only. if you see httponly in enabled but we expect secure attribute as well.
Once all call get completed. we could see all cookies in application tab in browser. There we expecting ‘Secure’ is ticked same as httponly.
using websdk only. As per my attachment during the start call NSC_ has both httponly and secure selected. But all other 3 cookie doesnt have ‘secure’ enabled. I am referring that issue.
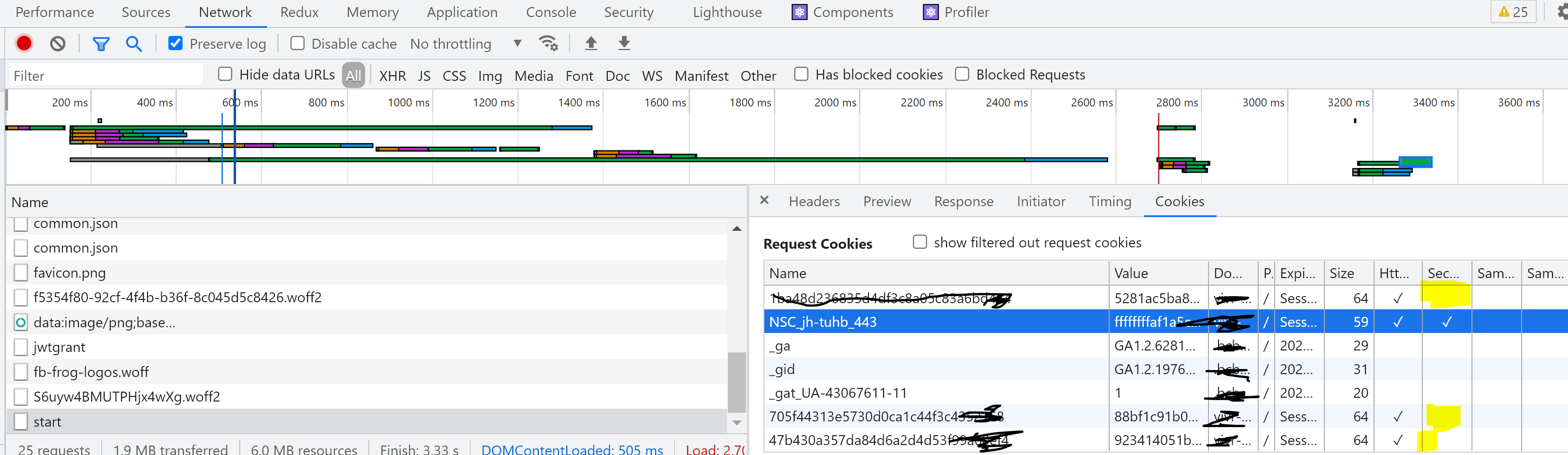
@swagata.sengupta did you get a chance to see that pls ?
@senthilkumar.muruges
I initiated an internal discussion with the architecture team on the secured attribute.
But without the secured attribute how does it impact you or your organisation functionally? Can you please share some insight on that? Do you see any vulnerability? If yes please report the same with details to koresupport@kore.com
@swagata.sengupta As per Security Vulnerability Testing (SVT) we should have secured attribute. This is blocking to deploy in to production environment.
@senthilkumar.muruges
Are you using an on premise version or our cloud ( bots.kore.ai )
Can you please send a detailed email with vulnerability findings and functional impact to koresupport@kore.com ? Please mention the url of this thread too.
Btw ever security vulnerability finding must have details on how it can be exploited. Please mention it in your email. Otherwise it will be difficult to take it up with our information security team.



